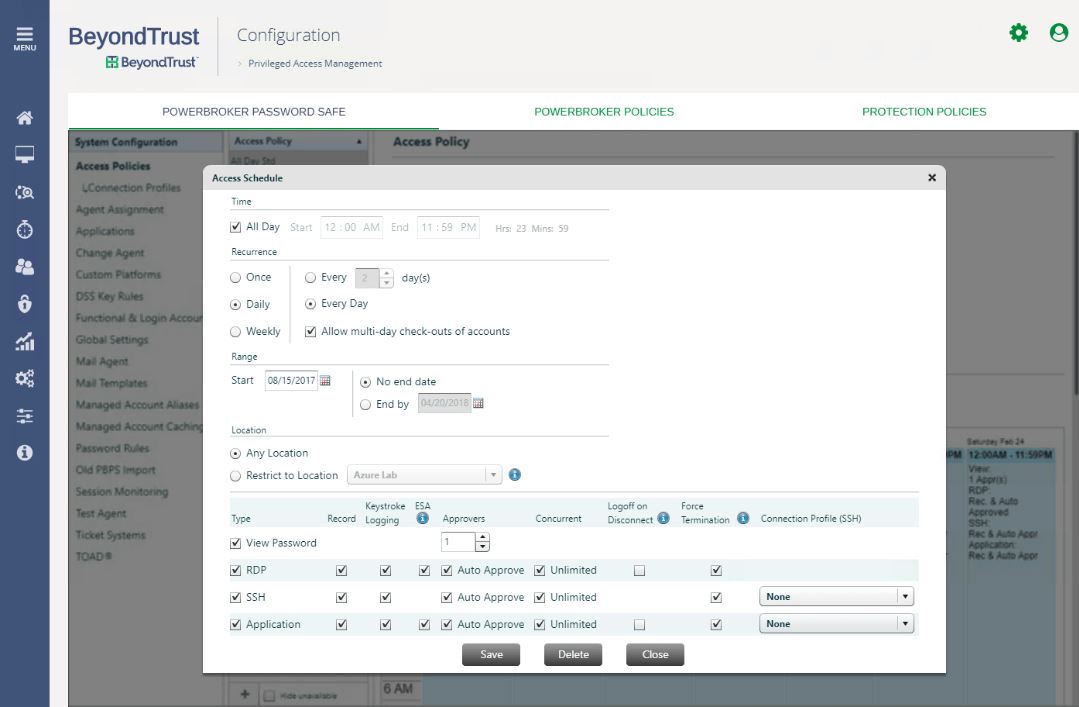
Permissions are often granted globally to individuals based upon job role, and do not take into account real-time risk factors such as location, day or time. Password Safe enables the dynamic assignment of just-in-time privileges via the Advanced Workflow Control engine.
Policies can be extended to block password access to some managed resources unless the request originated from the corporate network, or only allow access to certain vendor accounts if they originate from the vendor network.
Having this capability ensures that users have the right access according to the context of their request, thereby minimizing opportunities for exploiting privileged credentials.
Applications Passwords: Securing Application Credentials
Password Safe eliminates hard-coded or embedded application credentials automatically, simplifying management for IT and better securing the organization from exploitation of those credentials. Password Safe:
Enables removal of hard-coded passwords from applications and scripts
Provides an extensible REST interface that supports many languages, including C/C++, Perl .NET, and Java
Ensures that passwords can be automatically reset upon release
Enforces extensive security controls to lock down access to only authorized applications
Discovery: Complete, Automated Discovery and Onboarding of All Privileged Accounts
Password Safe leverages a distributed network discovery engine to scan, identify and profile all assets. Dynamic categorization of all assets and accounts enables auto-onboarding, and the ability for access policies to self-adjust according to environmental changes. This capability helps IT keep pace with changing environmental variables, reduces time and administrative overhead, and reduces risk by ensuring that no system is left unmonitored/unmanaged.
Discover and profile all known and unknown assets (web, mobile, cloud, virtual), privileged user accounts, shared accounts, and service accounts
Automatically bring systems and accounts under management
Create Smart Groups to automatically categorize, group, assess, and report on assets by IP range, naming convention, OS, domain, applications, business function, Active Directory, and more.
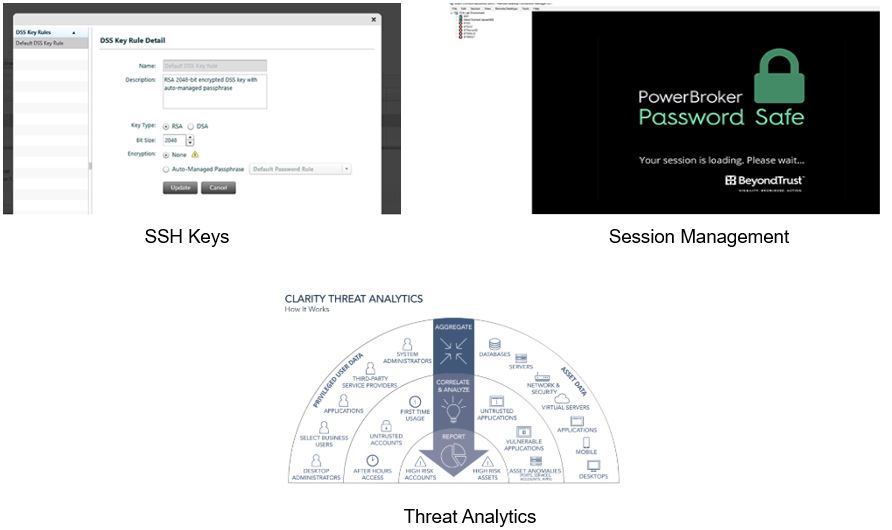
Session Management: Agentless Privileged Session Management
Privileged session monitoring and management is essential to achieve your compliance and security requirements, but can be complex and time-consuming to achieve. Many alternatives in the market force you to use Java, which is a notorious security risk, or require you to purchase additional licenses of what should be free tools.
Password Safe privileged session management uses standard desktop tools such as PuTTY and Microsoft Terminal Services Client, ensuring administrators can leverage commonly used management tools without the need for Java. With Password Safe, administrators can:
Request RDP/SSH access to authorized systems only
Start sessions instantly, or via workflow
View any active privileged session, and if required, pause or terminate the session
Use keystroke indexing and full text search to pinpoint data, and then log an acknowledgement of the review for audit purposes
Avoid Java – Password Safe is a client-less solution with no agents required on the server
Fully integrate with native tools (MSTSC, PuTTY, MobaXterm etc.)
Gain full video recording with 100% accountability
SSH Keys: Simplified SSH Key Management
Traditional methods of SSH key management are very labor intensive, with many organizations not properly rotating their keys. As well, it is common practice for administrators to share keys. Between the lack of rotation and the sharing of keys, organizations lose accountability over their systems, which could lead to those systems being vulnerable to exploits. Password Safe adds security and simplifies the management of SSH keys by:
Storing private keys like any other privileged credential
Automatically rotating SSH keys according to a defined schedule
Allowing designated ‘secondary’ accounts and SSH keys to be grouped to a ‘primary’ account to manage rotation interval, complexity and duration of SSH keys
Enforcing granular access control and workflow
Alerting when a key is released
Automatically logging users onto Unix or Linux systems through the proxy with no user exposure
Recording every privileged session with full playback and key usage auditing
Offering failover to a managed password for complete redundancy
Allowing SSH sessions to be easily established via your existing desktop tools without having to initiate with a web interface
Password Safe greatly simplifies the management and secures the use of SSH keys for better control, accountability and security over Unix and Linux systems.
Threat Analytics: Combine User, Account, and Asset Threat Analytics for Unmatched Visibility
Analyze privileged password, user, and account activity, along with asset characteristics such as vulnerability count, vulnerability level, attacks detected, risk score, applications, services, software and ports. Included malware analysis capabilities help you correlate application, service, and process data with a continuously updated malware database. BeyondTrust connects the dots and flags the events you need to focus on, allowing you to act decisively and effectively prioritize risk mitigation.
Aggregate user and asset data to baseline and track behavior
Correlate asset, user and threat activity to reveal critical risks
Identify potential malware threats buried in asset activity data
Increase the ROI of your existing security solutions
Generate reports to inform and align security decisions


















Văn phòng Hà Nội
Địa chỉ: D0802 Việt Đức Complex, 39 Lê Văn Lương, Phường Thanh Xuân, Thành phố Hà Nội, Việt Nam
Điện thoại: +84-24-6663 5757 - Fax: +84-24-6663 5758
Email: info@svtin.net - Website: www.svtin.net
Văn phòng Hồ Chí Minh
Địa chỉ: 1201 Hoàng Sa, Phường Tân Sơn Nhất, Thành phố Hồ Chí Minh, Việt Nam.
Điện thoại: +84-28-3846 0204 - Fax: +84-28-3846 0206
Email: info@svtin.net - Website: www.svtin.net