Solution Features
Operationalize Security Intelligence
Splunk Enterprise Security (ES) enables security teams to use all data to gain organization-wide visibility and security intelligence. Regardless of deployment model—on-premises, in a public or private cloud, SaaS, or any combination of these—Splunk ES can be used for continuous monitoring, incident response, running a security operations center or for providing executives a window into business risk.
Splunk ES provides organizations the ability to:
Improve security operations with faster response times
Improve security posture by getting end-to-end visibility across all machine data
Increase detection and investigation capabilities using advanced analytics
Make better informed decisions by leveraging threat intelligence
Improve Security Posture
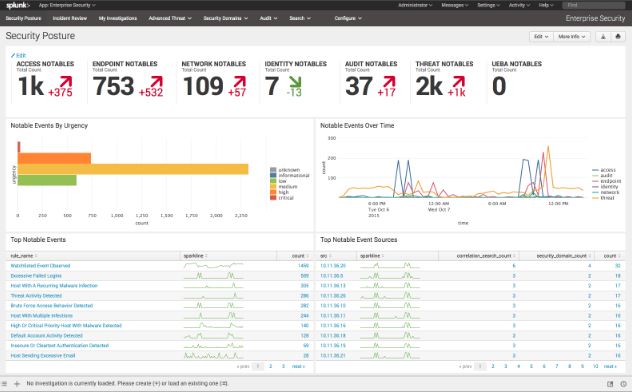
Security Posture: Get a library of security posture widgets to place on any dashboard or easily create your own. See security events by location, host, source type, asset groupings and geography. KPIs provide trending and monitoring of your security posture.
Incident Review and Classification: View a single event or get a roll-up of related system events and an incident management workflow for security teams. Easily verify incidents, change their status and criticality, and transfer among team members, all while supplying mandatory comments about status changes. Status changes are audited, monitored and tracked for team metrics. From within the incident review view, analysts can now use risk scores and in-context searches to determine the impact of an incident quickly and to generate actionable alerts to respond on matters that require immediate attention.
Built on a Big Data Platform for Security Intelligence: Spunk ES leverages Splunk Enterprise capabilities that include:
Index Any Data Source: The ability to bring in any data without custom connectors or vendor support enables analysts to quickly access, search and analyze the data they need to complete their investigation.
Scalability: The ability to index hundreds of terabytes of data per day. Splunk does not apply a schema at the time data is indexed and searches across terabytes of data can be performed quickly.
Flexible Dashboards: Dashboards can be easily created or customized for a quick graphical view of any data or correlation that is important to the organization. Organize multiple dashboards on a single screen for a customized view of the organization’s overall security posture.
Ad Hoc Searches: Ad hoc searches enable security teams to quickly understand what attacks are occurring in their environment to determine the best course of action.
Improve Security Operations
Customizable Dashboards: Create your own security portal based on your role and the things that matter to your organization. Organize and correlate multiple data sources visually in a single user interface to find relationships and gain context.
Asset Investigator: Visually correlate events over time for any IP address. This helps the analyst gain insight into time relationships across events.
Unified Search Editor: Use a user-friendly, consistent search creation experience—including guided searches—for key security indicator or key performance indicator correlation searches, and identity and asset investigation visualizations.
Statistical Analysis: Pre-built dashboards will help you identify anomalies in event and protocol data. The dashboards are pre-built using auto-configuring thresholds and baselines.
Incident Review, Classification and Investigation: Splunk ES provides comprehensive incident review capabilities that include:
Drill down from graphical elements to raw data and wire data captures to gain an understanding of all network communications
Unique workflow actions that augment the security investigation process and allow you to pivot on a single piece of common information—or any other data—to rapidly develop the threat context
Classification that allows for bulk event reassignment, changes in status and criticality classification, with all analyst activity available for auditing purposes
Incident Review Audit: For governance, auditing and protection against tampering, Splunk ES provides reports on all Splunk user and system activities for a complete audit trail. The Splunk platform uses data signing to maintain chain-of-custody and detect any alterations to the original log and event data.
Extreme Search: With Extreme Search commands, security relevant information is available to security analysts at a greater level of depth and precision than when relying on quantitative measurements alone. Because counts, rates and thresholds are calculated using a dynamically updating model, analysts don't have to manually adjust these values to get accurate results. Extreme Search also allows premium Splunk apps to offer key indicators and reports with easy to understand language cues, which are more contextual to the user than absolute numbers.
Detect Internal and Advanced Threats
Asset Center/Identity Center: Understanding where assets are, who owns them, their criticality and who should be accessing information on systems helps prioritize security events and investigations. Splunk software has the ability to perform lookups of data stored in an asset database, active directory, spreadsheet or CSV file and use that information as context for security events in reports and dashboards.
Advanced Threat Investigation: Use a variety of advanced detection and investigative controls for investigative purposes or to detect abnormal activity that’s often associated with compromised systems. This includes DNS new domain analysis, HTTP category and user agent analysis, traffic size analysis, URL length analysis, and threat intelligence artifacts.
Visual Anomaly Detection: View event data in the form of swim lanes and use heat maps to quickly identify anomalous behaviors and trends related to assets and identities in the environment. Out-of-the-box swim lanes include authentications, endpoint changes, threat list activity, IDS attacks, malware attacks, notable events and risk modifiers related to the user. Swim lanes can be modified to provide user activity profiling across any network, endpoint, access, identity and threat intelligence source.
Protocol Intelligence: Get information from the wire that’s either in lieu of, or complementary to, data from the endpoint or network, or could otherwise not be obtained. Provides protocol information supported by the Splunk Stream including SSL, DNS and email activity.
Integration with Splunk UBA
Splunk ES is integrated with Splunk UBA. Threats detected by Splunk UBA will show up as alerts in Splunk ES Incident Review dashboards to support Security Operations workflows.
The UBA detected anomalies are now available as a sourcetype within Splunk ES, which can be used as a starting point of the investigation, do ad hoc searching and pivot for detailed incident review and breach analysis.
For incidents that have UBA anomalies associated with them, users can now view specific details on the source of the anomalies within Splunk ES. Splunk UBA anomalies and threats are now available as Asset Investigator correlation searches (swim lanes).
UBA Anomalies: The UBA anomalies can be used for multiple SIEM workflows to deter and resolve threats quicker and with greater precision. Hunters and analysts can now use the UBA detected anomalies as a source type within Splunk ES as a starting point of the investigation, do ad hoc searching and pivot for detailed Incident Review and Breach Analysis.
Identify, Prioritize and Manage Security Events
Splunk ES delivers a flexible yet powerful security framework that enables security teams to:
Manage Alerts
Assign Risk
Operationalize Threat Intelligence
Quickly Identify Security Events
Understand Identity and Privilege Levels
Access Protection
Endpoint Protection
Network Protection
Make Better Informed Decisions
Enhance incident response and investigations by leveraging and correlating data from a broad set of sources, including security and non-security data collected from across the organization, and supplemented with internal and external threat intelligence and other contextual information.
Splunk ES leverages Splunk Enterprise to bring in any data without custom connectors or vendor support, enabling new data sources to be utilized quickly and easily, without expensive and time-consuming professional services engagements. In addition, Splunk ES natively supports emerging threat intelligence sharing standards such as STIX, TAXII, Department of Homeland Security’s (DHS) Automated Indicator Sharing (AIS), and openIOC. Threat Intelligence feeds can be operationalized by aggregating multiple sources, formats and retrieval mechanism, de-duplicating the information and then alerting on them as well as extracting the values for use in investigations as well as for downstream actions.
Optimize Incident Response
Streamline investigations of dynamic, multi-step attacks and more easily see the relative time relationship between the various events to determine root cause and next steps. Facilitate collaboration across the organization by enabling any security team member to place events, actions and annotations onto a timeline to share their perspective of the scenario.
Investigator Journal
Track searches and activities
Review activities at any point
Select and place into timeline for temporal analysis
Help remember searches, steps taken, provide annotation support
Investigation Timeline
The Investigation Timeline enables analysts to investigate the sequence of events using the kill chain methodology to determine the attack lifecycle. At any point in the investigation they can add relevant actions from the Investigator Journal, as well as raw events and even their own notes, to a timeline. This enables them to visualize and more clearly understand the attack details, as well as the sequential relationship between various events – and quickly determine the appropriate next steps.
The timeline makes it easy to collaborate with team members and other security personnel throughout the organization. In addition to being able to click through the entire report to get the original analyst’s perspective, any security team member can place events, actions and annotations into a timeline to share their perspective on the scenario.
The investigative reporting feature combines the raw event, actions, annotation notes and investigators involved with the incident so that team members can scroll through the details to understand the sequencing and time relationships of multiple events. This also helps executives and new analysts understand how attacks occurr in their environment and how to investigate them.





















Ha Noi Office
Address: 3rd floor, HH2 Bac Ha building, 15 To Huu, Thanh Xuan Ward, Hanoi City, Vietnam.
Tel: +84-24-6663 5757 - Fax: +84-24-6663 5758
Email: info@svtin.net - Website: www.svtin.net
Ho Chi Minh Office
Address: 1201 Hoang Sa, Tan Son Nhat Ward, Ho Chi Minh City, Vietnam.
Tel: +84-28-3846 0204 - Fax: +84-28-3846 0206
Email: info@svtin.net - Website: www.svtin.net